The following sections introduce some basic concepts relating to the operation of wireless networks, including data transmission.
The topics to be covered include:
- radio spectrum of wireless networks;
- access methods of wireless networks;
- association process of wireless networks.
Radio spectrum
Like all networks, wireless networks transmit data over a network medium. The medium is a form of electromagnetic radiation. The wireless spectrum is a continuum of electromagnetic waves used for data and voice communication. On the spectrum, waves are arranged according to their frequencies. The wireless spectrum spans frequencies 9KHz and 300 GHz, which is shown in Figure 1.1.
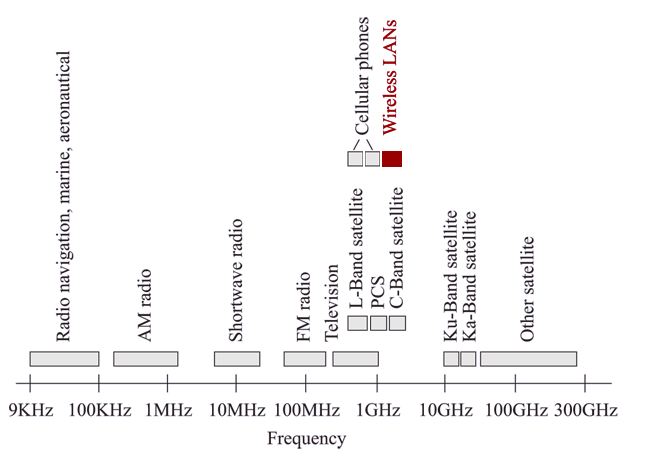
Radio waves can penetrate most office obstructions and offer a wider coverage range. It is no surprise that most, if not all, 802.11 products on the market use the radio wave physical layer.
Frequency bands used by 802.11 products
802.11b and 802.11g use the 2.4 GHz frequency band, while 802.11a uses the 5GHz frequency band.
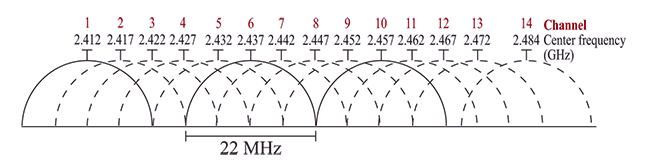
802.11 divides each of the frequency bands into channels, analogously to how radio and TV broadcast bands are sub-divided, but with greater channel width and overlap. For example the 2.4000–2.4835 GHz band is divided into 13 channels each of width 22 MHz but spaced only 5 MHz apart, with channel 1 centred on 2.412 GHz and channel 13 on 2.472 GHz, to which Japan adds a 14th channel, i.e. 12 MHz above channel 13.
Access methods
802.11 does not depart from the previous IEEE 802 standards in any radical way. The standard successfully adapts Ethernet-style networking to radio links. Like Ethernet, 802.11 uses a Carrier Sense Multiple Access (CSMA) scheme to control access to the transmission medium. However, collisions waste valuable transmission capacity, so rather than implementing the collision detection (CSMA/CD) employed by Ethernet, 802.11 uses collision avoidance (CSMA/CA). Also like Ethernet, 802.11 uses a distributed access scheme with no centralized controller. Each 802.11 station uses the same method to gain access to the medium.
Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA)
In CSMA/CA, before a node begins to send data, it checks the medium.
If it detects no transmission activity, it waits a brief, random amount of time, and then sends its transmission. If the node does detect activity, it waits a brief period of time before
checking the channel again. CSMA/CA does not eliminate the potential for collisions— it only minimizes them. This is the major difference between CSMA/CA and CSMA/CD (used by Ethernet).
In CSMA/CD, when a node finds out that the medium is idle, the node immediately starts to send data, but in CSMA/CA it waits for a brief, random amount of time before doing so.
The major differences between 802.11 and Ethernet therefore stem from the differences in the underlying medium. To tackle the vulnerability of wireless communications to external interference, 802.11 incorporates positive acknowledgments to ensure the reliable transmission of data.
Association
At any physical location – whether it is an Internet cafe, airport lounge, etc. — there could be many different wireless networks providing network coverage. A user therefore has to go through an association process to establish a link with a particular existing wireless network before he can use it to transmit data.
Association process of a wireless network
In order to establish a link with a particular existing wireless network for transmitting data, a user has to go through an association process.
Each wireless network is identified with a SSID (Service Set Identifier) — that is, a unique character string through which he can decide which wireless network he wants to associate with. During the association, the access point (AP) of the wireless network may or may not (depending on how the security protection is configured) authenticate the user before granting him access to the network connectivity.
The security protection described in the animation will be discussed further in a later part of this module.
This web page shows you some information about an access point product, for your reference.
Now read the following material and attempt Self-test 1 afterwards. While Suggested answers to Self-test 1 are provided, you should always try to answer the questions on your own first. If you can’t answer a particular question, this shows that you most likely need to review some of the material that you’ve worked through so far.
Reading
Dean (2010) 364–73.
Do you know you can improve your Wi-Fi connection without spending much? See Activity 1 and have a try!
- 4362 reads






