Encryption is the process of transforming messages or data to protect their meaning. Encryption scrambles a message so that it is meaningful only to the person knowing the method of encryption and the key for deciphering it. To everybody else, it is gobbledygook. The reverse process, decryption, converts a seemingly senseless character string into the original message. A popular form of encryption, readily available to Internet users, goes by the name of Pretty Good Privacy (PGP) and is distributed on the Web. PGP is a public domain implementation of public-key encryption.
Traditional encryption, which uses the same key to encode and decode a message, has a very significant problem. How do you securely distribute the key? It can't be sent with the message because if the message is intercepted, the key can be used to decipher it. You must find another secure medium for transmitting the key. So, do you fax the key or phone it? Either method is not completely secure and is time-consuming whenever the key is changed. Also, how do you know that the key's receiver will protect its secrecy?
A public-key encryption system has two keys: one private and the other public. A public key can be freely distributed because it is quite separate from its corresponding private key. To send and receive messages, communicators first need to create separate pairs of private and public keys and then exchange their public keys. The sender encrypts a message with the intended receiver's public key, and upon receiving the message, the receiver applies her private key (see Figure 2.5). The receiver's private key, the only one that can decrypt the message, must be kept secret to permit secure message exchange.
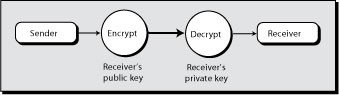
The elegance of the public-key system is that it totally avoids the problem of secure transmission of keys. Public keys can be freely exchanged. Indeed, there can be a public database containing each person's or organization's public key. For instance, if you want to e-mail a confidential message, you can simply obtain the sender's public key and encrypt your entire message prior to transmission.
|
To: George Zinkhan <gzinkhan@cbacc.cba.uga.edu> From: Rick Watson <rwatson@uga.edu> Subject: Money –––––––––––––––––––––––––––––– G'day George I hope you are enjoying your stay in Switzerland. Could you do me a favor? I need USD 50,000 from my secret Swiss bank account. The name of the bank is Aussie-Suisse International in Geneva. The account code is 451-3329 and the password is `meekatharra' I'll see you (and the money) at the airport this Friday. Cheers Rick |
Consider the message shown in Table 2.5; the sender would hardly want this message to fall into the wrong hands. After encryption, the message is totally secure (see Table 2.6). Only the receiver, using his private key, can decode the message.
|
To: George Zinkhan <gzinkhan@cbacc.cba.uga.edu> From: Rick Watson <rwatson@uga.edu> Subject: Money –––––––––––––––––––––––––––––– ––-BEGIN PGP MESSAGE––- Version: 2.6.2 hEwDfOTG8eEvuiEBAf9rxBdHpgdq1g0gaIP7zm1OcHvWHtx+9++ip27q6vI tjYbIUKDnGjV0sm2INWpcohrarI9S2xU6UcSPyFfumGs9pgAAAQ0euRGjZY RgIPE5DUHG uItXYsnIq7zFHVevjO2dAEJ8ouaIX9YJD8kwp4T3suQnw7/d 1j4edl46qisrQHpRRwqHXons7w4k04x8tH4JGfWEXc5LB+hcOSyPHEir4EP qDcEPlblM9bH6 w2ku2fUmdMaoptnVSinLMtzSqIKQlHMfaJ0HM9Df4kWh+ ZbY0yFXxSuHKrgbaoDcu9wUze35dtwiCTdf1sf3ndQNaLOFiIjh5pis+bUg 9rOZjxpEFbdGgYpcfBB4rvRNwOwizvSodxJ9H+VdtAL3DIsSJdNSAEuxjQ0 hvOSA8oCBDJfHSUFqX3ROtB3+yuT1vf/C8Vod4gW4tvqj8C1QNte+ehxg== =fD44 ––-END PGP MESSAGE––- |
- 2261 reads






