In addition, a public-key encryption system can be used to authenticate messages. In cases where the content of the message is not confidential, the receiver may still wish to verify the sender's identity. For example, one of your friends may find it amusing to have some fun at your expense (see Table 2.7).
|
To: Rick Watson <rwatson@uga.edu> From: President@whitehouse.gov Subject: Invitation to visit the White House –––––––––––––––––––––––––––––– Dear Dr. Watson It is my pleasure to invite you to a special meeting of Internet users at the White House on April 1st at 2pm. Please call 212-123-7890 and ask for Mr. A. Phool for complete details of your visit. The President |
If the President indeed were in the habit of communicating electronically, it is likely that he would sign his messages so that the receiver could verify it. A sender's private key is used to create a signed message . The receiver then applies the sender's public key to verify the signature (see Figure 2.6).
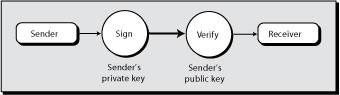
A signed message has additional encrypted text containing the sender's signature (see Table 2.8). When the purported sender's public key is applied to this message, the identity of the sender can be verified (it was not the President).
|
To: Rick Watson <rwatson@uga.cc.uga.edu> From: President@whitehouse.gov Subject: Invitation to visit the White House –––––––––––––––––––––––––––––– Dear Dr. Watson It is my pleasure to invite you to a special meeting of Internet users at the White House on April 1st at 2pm. Please call 212-123-7890 and ask for Mr. A. Phool for complete details of your visit. The President ––-BEGIN PGP SIGNATURE––- Version: 2.6.2 iQCVAwUBMeRVVUblZxMqZR69AQFJNQQAwHMSrZhWyiGTieGukbhPGUNF3aB +qm7E8g5ySsY6QqUcg2zwUr40w8Q0Lfcc4nmr0NUujiXkqzTNb+3RL41w5x fTCfMp1Fi5Hawo829UQAlmN8L5hzl7XfeON5WxfYcxLGXZcbUWkGio6/d4r 9Ez6s79DDf9EuDlZ4qfQcy1iA==G6jB ––-END PGP SIGNATURE––- |
Imagine you pay USD 1,000 per year for an investment information service. The provider might want to verify that any e-mail requests it receives are from subscribers. Thus, as part of the subscription sign-up, subscribers have to supply their public key, and when using the service, sign all electronic messages with their private key. The provider is then assured that it is servicing paying customers. Naturally, any messages between the service and the client should be encrypted to ensure that others do not gain from the information.
- 2157 reads






