|
1. |
You worked with the Causeway Company cash receipts system in Documenting Business Processes and Information Systems. The narrative of that system and its systems flowchart are reproduced in Table 9.5 and Figure 9.12, respectively. Using Table 9.5 and Figure 9.12, do the following: a. Prepare a control matrix, including explanations of how each recommended existing control plan helps to accomplish—or would accomplish in the case of missing plans—each related control goal. Your choice of recommended control plans should come from Table 9.2, Table 9.3, or Table 9.4 as appropriate. Be sure to tailor the matrix columns to conform to the specifics of the Causeway system. In doing so, assume the following two operations process goals only:
b. Annotate the systems flowchart in Figure 9.12 to show the location of each control plan you listed in the control matrix.
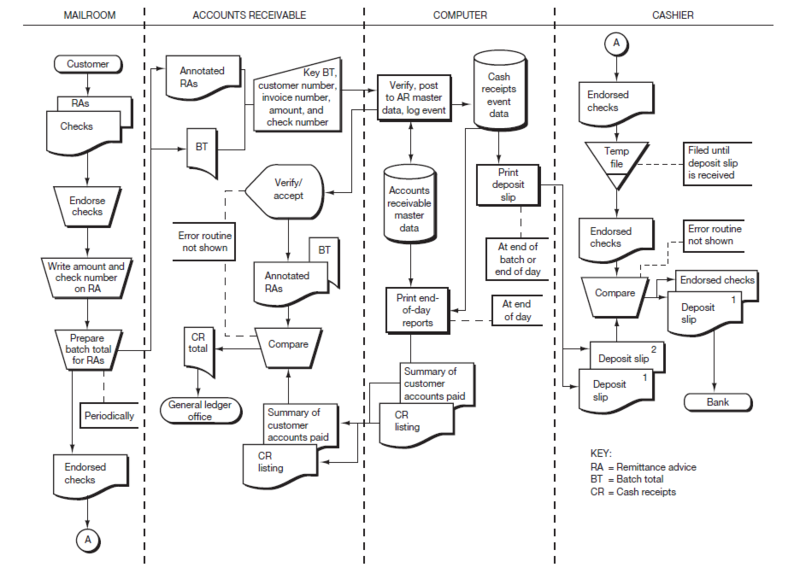
Figure 9.12 Causeway Company Systems Flowchart to Accompany Problem 9-1
|
||||||||||||||||
|
2. |
The following narrative describes the processing of customer mail orders at Phoenix Company. Phoenix Company is a small manufacturing operation engaged in the selling of widgets. Customer mail orders are received in the sales order department, where sales order clerks open the orders and review them for accuracy. The clerks enter each order into the computer, where they are edited by comparing them to customer master data (stored on a disk). The computer displays the edited order on the clerk’s screen. The clerk reviews and accepts the order. The order is then added to the sales event data (stored on a disk) and updates the sales order master data (also stored on a disk). As the order is recorded, it is printed on a printer in the warehouse (the picking ticket). A copy of the sales order is also printed in the sales order department and is sent to the customer (a customer acknowledgment). (Complete only those requirements specified by your instructor) a. Prepare a table of entities and activities. b. Draw a context diagram. c. Draw a physical data flow diagram (DFD). d. Indicate on the table of entities and activities prepared for part a, the groupings, bubble numbers, and titles to be used in preparing a level 0 logical DFD. e. Draw a level 0 logical DFD. f. Draw a systems flowchart. g. Prepare a control matrix, including explanations of how each recommended existing control plan helps to accomplish—or would accomplish in the case of missing plans—each related control goal. Your choice of recommended control plans should come from Table 9.2, Table 9.3, or Table 9.4 as appropriate. Be sure to tailor the matrix columns to conform to the specifics of the Phoenix Company system. In doing so, assume the following two operations process goals only:
h. Annotate the systems flowchart prepared in requirement f to show the location of each control plan listed in the control matrix. |
||||||||||||||||
|
3. |
The following is a list of 14 control plans from this chapter: Control Plans A. Populate inputs with master data B. Online prompting C. Interactive feedback checks D. Programmed edit checks E. Manual agreement of batch totals F. Batch sequence check G. Cumulative sequence check H. Document design I. Key verification J. Written approvals K. Procedures for rejected inputs L. Compare input data with master data M. Turnaround documents N. Digital signatures Listed below are 10 system failures that have control implications. On your solution sheet, list the numbers 1 through 10. Next to each number, insert the capital letter from the list above for the best control plan to prevent the system failure from occurring. (If you can’t find a control that will prevent the failure, then choose a detective plan or, as a last resort, a corrective control plan.) A letter should be used only once, with four letters left over. System Failures
|
||||||||||||||||
|
4. |
The following is a list of 12 controls from CONTROLLING INFORMATION SYSTEMS: PROCESS CONTROLS: Controls A. Turnaround documents B. Tickler files C. Public-key cryptography D. One-for-one checking E. Batch sequence check F. Document/record counts G. Written approvals H. Hash totals (for a batch) I. Limit checks J. Procedures for rejected inputs K. Digital signatures L. Interactive feedback checks Listed below are 10 definitions or descriptions. List the numbers 1 through 10 on your solution sheet. Next to each number, insert the capital letter from the list above for the term that best matches the definition. A letter should be used only once, with two letters left over. Definitions or Descriptions
|
||||||||||||||||
|
5. |
The following is a description of seven control/technology descriptions and a list of seven control/technology names.
Listed below are five potential risks or systems failures that can be addressed with a control or a technology from the lists above. A. On the blank line to the left of each number (the “Description” column), insert the capital letter from the list above for the control/technology that bestaddresses the risk. A letter should be used only once, with two letters left over. B. In the column titled “Explanation,” provide an explanation of why you selected that control/technology description. You need to specifically describe how the control/technology addresses the risk. C. In the right column (titled “Name”) insert the number from the list above corresponding to the control/technology name for the answer provided in part A. |
| DESCRIPTION | POTENTIAL RISKS | EXPLANATION | NAME |
| a. A computer programmer altered the order entry programs so that the credit-checking routine was bypassed for one of the customers, a company owned by his uncle. | |||
| b. A hacker accessed the Web site at Dorothy’s Gifts & Flowers and changed some of the graphics. Several customers, confused by the graphics, took their business elsewhere. | |||
| c. Roxy’s Retailing maintains an extensive and valuable repository of information about its customers. Tricky Nick was fired from Roxy’s and now works at a competing firm. Last night Nick dialed into the Roxy computer system and downloaded some valuable customer data to his own computer. | |||
| d. Cash application clerks at the Blanford Company have been posting payments to the incorrect customer accounts because the customer account numbers are being keyed in incorrectly. | |||
| e. At Natick Company, customers who are four months late in making payments to their accounts are still able to have their orders accepted and goods shipped to them. |
- 8175 reads






