|
|
Data encryption is a process that employs mathematical algorithms and encryption “keys” to change data from plain text to a coded text form so that it is unintelligible and therefore useless to those who should not have access to it. Encryption is useful to preserve the data’s privacy and confidentiality. For example, people are asking for and obtaining security of their Internet transmissions through cryptography. Technology Application 9.1 (at the end of this Appendix) describes three methods for conducting secure electronic commerce on the Internet using data encryption and public-key cryptography. |
One of the earliest and most elementary uses of encryption dates back to the first century B.C. During the Gallic Wars, Julius Caesar encoded his messages by shifting the alphabet three letters forward so that an A became a D, an X became an A, and so on. For instance, if the message is NED IS A NERD—called plaintext in cryptography lingo—the ciphertextwould appear as QHG LV D QHUG. The Caesar cipher—an example of a simple one-for-one letter substitution system—in effect used a keyof 3 and an encrypting algorithm of addition. We see examples of this type of encryption in the cryptograms or cryptoquotes that are published in the puzzle pages of our daily newspapers.
With the use of more complex algorithms and encryption keys, coding a message can be made much more powerful than in the preceding example. Figure 9.10 contains an illustration of how the message NED IS A NERD could be made more difficult to decode. Keep in mind, however, that the figure also is a very basic, rudimentary example intended to convey the bare-bones mechanics of how encryption works. In practice, the algorithms and keys are much more sophisticated; so much so that good encryption schemes are virtually impossible to break.
As shown in Figure 9.10, the crux of conventional encryption procedures is the single key used both by the sender to encrypt the message and by the receiver to decrypt it. A major drawback to such systems is that the key itself has to be transmitted by secure channels. If the key is not kept secret, the security of the entire system is compromised. Public-key cryptography helps to solve this problem by employing a pair of matched keys for each system user, one private (i.e., known only to the party who possesses it) and one public. The public key corresponds to—but is not the same as—the user’s private key. As its name implies, the public key is assumed to be public knowledge and even could be published in a directory, in much the same way as a person’s telephone number.
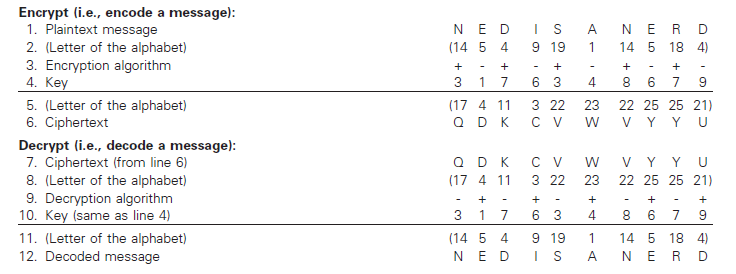
Figure 9.11 illustrates how public-key cryptography is used both to encrypt messages (part (a) of the figure) and to authenticate a message by appending a digital signature to it (part (b) of the figure). Please note that although we show both parts (a) and (b) being executed, in practice the parts are separable. That is, a message could be encrypted as shown in part (a) without having a digital signature added to it. Digital signatures enhance security by ensuring that the “signature” cannot be forged (i.e., that the message comes from an authorized source) and that the message has not been changed in any way in transmission.
Note that Sally Sender and Ray Receiver each have a pair of keys. In part (a), Ray’s public key is used to encrypt all messages sent to him. Privacy of the messages is ensured because only Ray’s private key can decrypt the messages. The messages cannotbe decoded using Ray’s public key. Furthermore, the private decryption key never has to be transmitted; it is always in Ray’s exclusive possession.
In part (b), Sally first uses a hashing function to translate the plaintext message into a binary number. Any message other than NED IS A NERD would not “hash” into the number, 11010010. By then using her private key to encrypt the binary number, Sally, in effect, has digitally “signed” the message. On the right side of part (b), Ray Receiver employs Sally’s public key to decrypt her “signature.” Since no public key except Sally’s will work, Ray knows that the message comes from her. Note that anyone could use Sally’s public key to decode her signature, but that is not important. The object is not to keep the signature secret or private but, rather, to authenticatethat it was Sally—and only she—who “signed” the message.
To ensure the integrity of the message (received in part (a) of the figure), Ray
- runs the decrypted message, NED IS A NERD, through an encoding scheme called a hashing function—the same hashing function used by Sally—and
- compares the decoded digital signature (11010010) with the hashed output of the message received (11010010). If the two numbers don’t agree, Ray knows that the message is not the same as the one Sally sent. For example, assume that Ted Tamperer was able to intercept Sally’s encrypted message in part (a) and change it so that when Ray decoded it, he read NED IS A NICE GUY. This message would not hash into the number 11010010; therefore, it would not match the decrypted digital signature from Sally.
|
|
Some experts predict that digital signatures will soon pave the way for a truly cashless society, talked about for years. The digital signatures will be used to create electronic cash, checks, and other forms of payment that can be used in electronic commerce (see Technology Application 9.1 on page 312 for examples). Others foresee digital signatures replacing handwritten ones on a multitude of business and legal documents, such as purchase orders, checks, court documents, and tax returns. The “E-sign” law, passed by Congress in June 2000, makes contracts “signed” by electronic methods legally valid in all 50 states. This law is accelerating the rate of growth of business-to-business (B2B) e-business by allowing companies to execute documents online immediately.1 (Review Technology Excerpt 8.4 for more on E-sign and digital signatures.) |
TECHNOLOGY APPLICATION 9.1
Using Data Encryption and Public-Key Cryptography for Electronic Commerce
Data encryption and public-key cryptography are being used to secure business transactions on the Internet. Below are three examples. The first two are in use, and the latter one was piloted until July 2001. The eCheck technology has been applied for online payments by firms such as Xign http://www.xign.com/) and Clareon (http://www.clareon.com). Only SSL is widely used.
Case 1: SSL
The secure sockets layer (SSL) protocol was developed by Netscape Communications Company (now owned by America Online) and uses public key cryptography to secure communications on the Internet. With SSL, a secure session is established during which messages transmitted between two parties are protected via encryption. For example, before a consumer transmits a credit card number to a merchant, the merchant’s server establishes a secure session. The merchant decrypts the message, extracts the credit card number, and submits a charge to the consumer’s credit card company (i.e., credit card issuing bank) to clear the transaction using traditional means. SSL protects the consumer from interception and unauthorized use of the purchase and credit card information while it is on the Internet (i.e., from the consumer’s Web browser to the merchant’s Web server). Normally, the merchant cannot authenticate the transmission to determine from whom the message originated and the consumer has only moderate assurance that they have sent their credit card number to a legitimate merchant.
Case 2: SET
The secure electronic transaction (SET) protocol was developed by MasterCard and Visa to secure credit card transactions on the Internet involving three parties: the consumer, the merchant, and one or more credit card issuing banks. With SET, the consumer separately encrypts the purchase message and the credit card number. The merchant decrypts the purchase message to proceed with the sale and submits a charge to the consumer’s credit card company (i.e., credit card issuing bank) to clear the transaction using traditional means. However, unlike SSL, SET-based clearing will pass through the merchant and go directly to the consumer’s credit card issuing bank. The consumer and the merchant sign their messages with certificates obtained from financial institutions that certify that the consumer holds the credit card in question and that the merchant has a credit card clearing relationship with the issuing bank. SET protects merchants and credit card issuing banks from unauthorized purchases, and consumers from credit card fraud.
Case 3: eCHECK
The electronic check (eCheck) is a payment mechanism developed by the Financial Services Technology Consortium (FSTC). Using public-key cryptography and digital signatures, trading partners and their banks can transmit secure messages and payment information. As with SET, eCheck certificates would be issued by banks certifying that the holder of the certificate has an account at that bank. And, payments would be processed automatically through the existing bank systems. Unlike SET, however, payments would be checks drawn on bank accounts. And, a feature beyond SSL and SET is that the eCheck protocol defines message formats, such as purchase orders, acknowledgments, and invoices, that can be processed automatically by trading parties. eCheck provides protections similar to those obtained with SET. That is, merchants and banks are protected from unauthorized use of checks, and the consumer is protected from check fraud.
Sources: For information about SSL, see, among other sites, the Netscape Web site at http://www.netscape.com/eng/ssl3/, March 18, 2002. For information about SET, see the MasterCard or SETCo (SET Secure Electronic Transaction LLC) Web sites at http://www.mastercardintl.com/newtechnology/set/ and http://www.setco.org/, March 18, 2002. For information about the FSTC electronic check project, see the eCheck Web site at http://echeck.commerce.net/ (March 18, 2002) or Ulric J. Gelinas, Jr. and Janis L. Gogan, “The FSTC Electronic Check Project,” American Institute of Certified Public Accountants Case DevelopmentProgram, 1996.
For public-key cryptography to be effective, the private keys must be kept private. To do that we can employ a variety of techniques, some of which were introduced in IT Governance: The Management and Control of Information Technology and Information Integrity. For example, the private key might be kept within a protected computer or device such as a smartcard, or cryptographic box. Access to the device, and to the private key, must then be protected with passwords or other authentication procedures. One such procedure involves the use of a thumbprint reader attached to the computer. With this device users must put their thumb onto the reader before the private key can be used to “sign” a message. The thumbprint reader is an example of the biometric devices introduced in IT Governance: The Management and Control of Information Technology and Information Integrity.
|
Review Question Distinguish among data encryption, public-key cryptography, and digital signatures. |
- 5886 reads







