Solution to Exercise 6.3.1
In both cases, the answer depends less on geometry than on material properties. For coaxial cable,
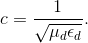
For twisted pair,
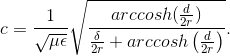
Solution to Exercise 6.3.2
You can find these frequencies from the spectrum allocation chart (Frequency Allocations). Light in the middle of the visible band has a wavelength of about 600 nm, which corresponds to a frequency of 5 × 1014Hz . Cable television transmits within the same frequency band as broadcast television (about 200 MHz or 2 × 108Hz ). Thus, the visible electromagnetic frequencies are over six orders of magnitude higher!
Solution to Exercise 6.3.3
As frequency increases,
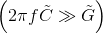
and
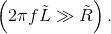
In this high-frequency region,
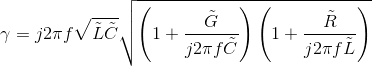
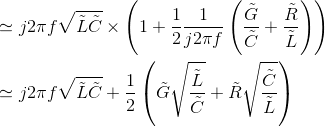
(6.65)
Thus, the attenuation (space) constant equals the real part of this expression, and equals
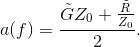
Solution to Exercise 6.4.1
As shown previously (Modulated Communication), voltages and currents in a wireline channel, which is modeled as a transmission line having resistance, capacitance and inductance, decay exponentially with distance. The inverse-square law governs free-space propagation because such propagation is lossless, with the inverse-square law a consequence of the conservation of power. The exponential decay of wireline channels occurs because they have losses and some filtering.
Solution to Exercise 6.5.1
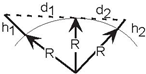
Use the Pythagorean Theorem, (h + R)2 = R2 + d2, where h is the antenna height, d is the distance from the top of the earth to a tangency point with the earth's surface, and R the earth's radius. The line-of-sight distance between two earth-based antennae equals
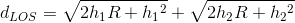
As the earth's radius is much larger than the antenna height, we have to a good approximation that
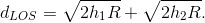
If one antenna is at ground elevation, say h2 =0 , the other antenna's range is
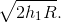
Solution to Exercise 6.5.2
As frequency decreases, wavelength increases and can approach the distance between the earth's surface and the ionosphere. Assuming a distance between the two of 80 km, the relation λf = c gives a corresponding frequency of 3.75 kHz. Such low carrier frequencies would be limited to low bandwidth analog communication and to low datarate digital communications. The US Navy did use such a communication scheme to reach all of its submarines at once.
Solution to Exercise 6.7.1
Transmission to the satellite, known as the uplink, encounters inverse-square law power losses. Reflecting of the ionosphere not only encounters the same loss, but twice. Refection is the same as transmitting exactly what arrives, which means that the total loss is the product of the uplink and downlink losses. The geosynchronous orbit lies at an altitude of 35700km. The ionosphere begins at an altitude of about 50 km. The amplitude loss in the satellite case is proportional to 2.8 × 10−8; for Marconi, it was proportional to 4.4 × 10−10. Marconi was very lucky.
Solution to Exercise 6.8.1
If the interferer's spectrum does not overlap that of our communications channel - the interferer is out-of-band we need only use a bandpass filter that selects our transmission band and removes other portions of the spectrum.
Solution to Exercise 6.9.1
The additive-noise channel is not linear because it does not have the zero-input-zero-output property (even though we might transmit nothing, the receiver's input consists of noise).
Solution to Exercise 6.11.1
The signal-related portion of the transmitted spectrum is given by
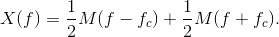
Multiplying at the receiver by the carrier shifts this spectrum to fc and to −fc, and scales the result by half.
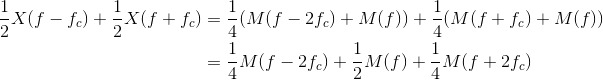
(6.67)
The signal components centered at twice the carrier frequency are removed by the lowpass filter, while the baseband signal M(f) emerges.
Solution to Exercise 6.12.1
The key here is that the two spectra M (f − fc), M (f + fc) do not overlap because we have assumed that the carrier frequency fc is much greater than the signal's highest frequency. Consequently, the term M (f − fc) M (f + fc) normally obtained in computing the magnitude-squared equals zero.
Solution to Exercise 6.12.2
Separation is 2W. Commercial AM signal bandwidth is 5 kHz. Speech is well contained in this bandwidth, much better than in the telephone!
Solution to Exercise 6.13.1
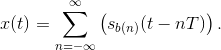
Solution to Exercise 6.14.1
k =4.
Solution to Exercise 6.14.2
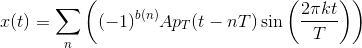
Solution to Exercise 6.14.3
The harmonic distortion is 10%.
Solution to Exercise 6.14.4
Twice the baseband bandwidth because both positive and negative frequencies are shifted to the carrier by the modulation: 3R.
Solution to Exercise 6.16.1
In BPSK, the signals are negatives of each other: s1 (t)= −s0 (t). Consequently, the output of each multiplier-integrator combination is the negative of the other. Choosing the largest therefore amounts to choosing which one is positive. We only need to calculate one of these. If it is positive, we are done. If it is negative, we choose the other signal.
Solution to Exercise 6.16.2
The matched filter outputs are 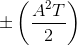
because the sinusoid has less power than a pulse having the same amplitude.
Solution to Exercise 6.17.1
The noise-free integrator outputs differ by αA2T , the factor of two smaller value than in the baseband case arising because the sinusoidal signals have less energy for the same amplitude. Stated in terms of Eb, the difference equals 2αEb just as in the baseband case.
Solution to Exercise 6.18.1
The noise-free integrator output difference now equals
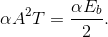
The noise power remains the same as in the BPSK case, which from the probability of error equation (6.46) yields
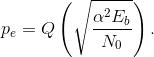
Solution to Exercise 6.20.1
Equally likely symbols each have a probability of 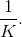 Thus,
Thus,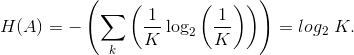 To prove that this is the maximum-entropy probability assignment, we must explicitly take into account that probabilities sum
to one. Focus on a particular symbol, say the first. Pr [a0] appears twice in the entropy formula: the terms Pr[a0]
log2Pr[a0]and (1 −Pr[a0]+ ··· + Pr[aK−2]) log2(1 −Pr
[a0]+ ··· + Pr [aK−2]) . The derivative with respect to this probability (and all the others) must be
zero. The derivative equals log2Pr [a0] − log2 (1 −Pr [a0]+ ··· +
Pr[aK−2]), and all other derivatives have the same form (just substitute your letter's index). Thus, each probability must equal the others, and we are
done. For the minimum entropy answer, one term is 1log21=0 , and the others are 0log20 , which we define to be zero also. The minimum value of entropy is zero.
To prove that this is the maximum-entropy probability assignment, we must explicitly take into account that probabilities sum
to one. Focus on a particular symbol, say the first. Pr [a0] appears twice in the entropy formula: the terms Pr[a0]
log2Pr[a0]and (1 −Pr[a0]+ ··· + Pr[aK−2]) log2(1 −Pr
[a0]+ ··· + Pr [aK−2]) . The derivative with respect to this probability (and all the others) must be
zero. The derivative equals log2Pr [a0] − log2 (1 −Pr [a0]+ ··· +
Pr[aK−2]), and all other derivatives have the same form (just substitute your letter's index). Thus, each probability must equal the others, and we are
done. For the minimum entropy answer, one term is 1log21=0 , and the others are 0log20 , which we define to be zero also. The minimum value of entropy is zero.
Solution to Exercise 6.22.1
The Huffman coding tree for the second set of probabilities is identical to that for the first (Figure 6.18 (Huffman Coding Tree)). The average code length is 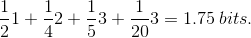 The entropy calculation 2
4 5 20 is straightforward:
The entropy calculation 2
4 5 20 is straightforward: 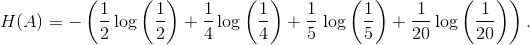 which equals 1.68 bits.
which equals 1.68 bits.
Solution to Exercise 6.23.1
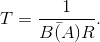
Solution to Exercise 6.23.2
Because no codeword begins with another's codeword, the first codeword encountered in a bit stream must be the right one. Note that we must start at the beginning of the bit stream; jumping into the middle does not guarantee perfect decoding. The end of one codeword and the beginning of another could be a codeword, and we would get lost.
Solution to Exercise 6.23.3
Consider the bitstream ...0110111... taken from the bitstream 0I10I110I110I111I.... We would decode the initial part incorrectly, then would synchronize. If we had a fxed-length code (say 00,01,10,11), the situation is much worse. Jumping into the middle leads to no synchronization at all!
Solution to Exercise 6.25.1
This question is equivalent to 3pe×(1 − pe)+pe2≤ 1 or
2pe2−3pe +1 ≥ 0. Because this is an upward-going parabola, we need only check where
its roots are. Using the quadratic formula, we find that they are located at  and 1. Consequently in the range
and 1. Consequently in the range 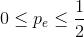 the error rate produced by coding is smaller.
the error rate produced by coding is smaller.
Solution to Exercise 6.26.1
With no coding, the average bit-error probability pe is given by the probability of error equation (6.47):
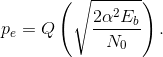
With a threefold repetition code, the bit-error probability is given by 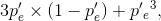 where
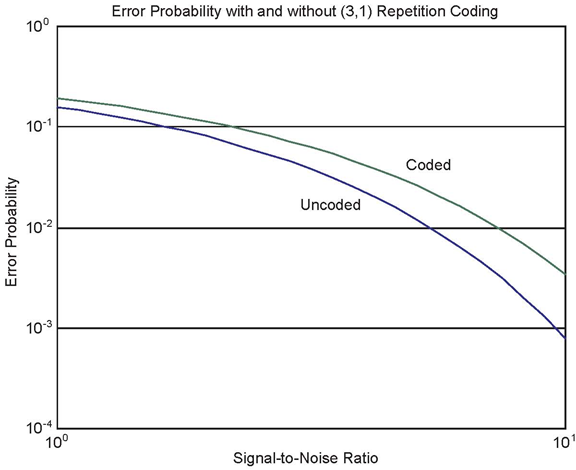
where 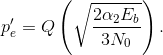 Plotting this reveals that the increase in bit-error probability out of the channel because of the energy reduction is not
compensated by the repetition coding.
Plotting this reveals that the increase in bit-error probability out of the channel because of the energy reduction is not
compensated by the repetition coding.
Solution to Exercise 6.27.1
In binary arithmetic (see 6.27 No Title Provided), adding 0 to a binary value results in that binary value while adding 1 results in the opposite binary value.
Solution to Exercise 6.27.2
dmin=2n +1
Solution to Exercise 6.28.1
When we multiply the parity-check matrix times any codeword equal to a column of G, the result consists of the sum of an entry from the lower portion of G and itself that, by the laws of binary arithmetic, is always zero.
Because the code is linear - sum of any two codewords is a codeword - we can generate all codewords as sums of columns of G. Since multiplying by H is also linear, Hc = 0.
Solution to Exercise 6.28.2
In binary arithmetic see this table, adding 0 to a binary value results in that binary value while adding 1 results in the opposite binary value.
Solution to Exercise 6.28.3
The probability of a single-bit error in a length-N block is Npe(1 − pe)N-1and a triple-bit error has probability
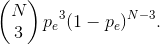
For the first to be greater than the second, we must have
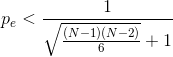
For N =7, pe< 0.31.
Solution to Exercise 6.29.1
In a length-N block, N single-bit and 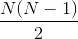 double-bit errors can
occur. The number of non-zero vectors resulting from
double-bit errors can
occur. The number of non-zero vectors resulting from 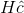 must equal or exceed
the sum of these two numbers.
must equal or exceed
the sum of these two numbers.
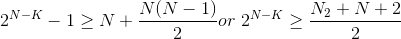
(6.68)
The first two solutions that attain equality are (5,1) and (90,78) codes. However, no perfect code exists other than the single-bit error correcting Hamming code. (Perfect codes satisfy relations like (6.68) with equality.)
Solution to Exercise 6.31.1
To convert to bits/second, we divide the capacity stated in bits/transmission by the bit interval duration T.
Solution to Exercise 6.33.1
The network entry point is the telephone handset, which connects you to the nearest station. Dialing the telephone number informs the network of who will be the message recipient. The telephone system forms an electrical circuit between your handset and your friend's handset. Your friend receives the message via the same device the handset that served as the network entry point.
Solution to Exercise 6.36.1
The transmitting op-amp sees a load or 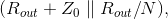 where N is the number of transceivers other than this one attached to the coaxial cable. The transfer function to some other transceiver's receiver circuit is Rout divided by this
load.
where N is the number of transceivers other than this one attached to the coaxial cable. The transfer function to some other transceiver's receiver circuit is Rout divided by this
load.
Solution to Exercise 6.36.2
The worst-case situation occurs when one computer begins to transmit just before the other's packet arrives. Transmitters must sense a collision before packet transmission ends. The time taken for one computer's packet to travel the Ethernet's length and for the other computer's transmission to arrive equals the round-trip, not one-way, propagation time.
Solution to Exercise 6.36.3
The cable must be a factor of ten shorter: It cannot exceed 100 m. Different minimum packet sizes means different packet formats, making connecting old and new systems together more complex than need be.
Solution to Exercise 6.37.1
When you pick up the telephone, you initiate a dialog with your network interface by dialing the number. The network looks up where the destination corresponding to that number is located, and routes the call accordingly. The route remains fixed as long as the call persists. What you say amounts to high-level protocol while establishing the connection and maintaining it corresponds to low-level protocol.
- 瀏覽次數:8168






