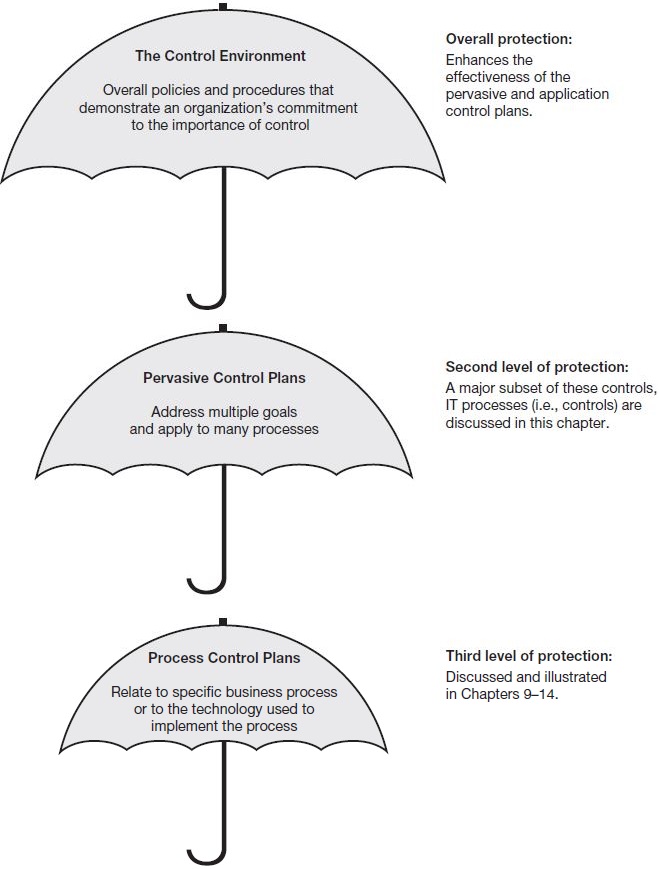
Control plans are information processing policies and procedures that assist in accomplishing control goals. Control plans can be classified in a number of different ways that help us to understand them. Figure 8.1 shows one such classification scheme—a control hierarchy that relates control plans to the control environment,defined earlier. The fact that the control environment appears at the top of the hierarchy illustrates that the control environment comprises a multitude of factors that can either reinforce or mitigate the effectiveness of the pervasive and process control plans.
The second level in the Figure 8.1 control hierarchy consists of pervasive control plans. Pervasive control plans relate to a multitude of goals and processes. Like the control environment, they provide a climate or set of surrounding conditions in which the various business processes operate. They are broad in scope and apply equally to all business processes—hence, they pervade all systems. For example, preventing unauthorized access to the computer system would protect all of the specific business processes that run on the computer (such as sales and marketing, billing, “purchase-to-pay,” business reporting, and so on). We discuss a major subset of these pervasive controls—IT processes (i.e., controls)—later in this chapter.
|
Review Question What is the difference between a process control plan, a pervasive control plan, and an IT control process? |
Process control plans are those controls particular to a specific process or subsystem, such as inventory or human resources, or to a particular mode of processing events, such as online or batch. Process control plans are the subject of the control framework introduced in Chapter 9.
Another useful and common way to classify controls is in relation to the timing of their occurrence. Preventive control plans stop problems from occurring. Detectivecontrol plans discover that problems have occurred. Corrective control plansrectify problems that have occurred. Let’s use the WTC tragedy to illustrate. By operating two computer processing sites—one primary and one mirror site—companies located in the WTC could prevent the loss of their computer processing capabilities and the data and programs stored on the computers located in the WTC (i.e., duplicate copies would reside at the mirror site). Smoke and fire detectors could detect fires in the building that inevitably lead to the loss of processing capabilities. Other monitoring devices could detect the loss of phones, data communications, and processing capabilities. These devices, operating at an organization’s facilities outside the WTC area, could have alerted company personnel to the loss of resources in the area of the WTC. Also, organizations can subscribe to services that will provide notification in the event of disaster. Finally, backup copies of programs and data could have been loaded onto computers at sites outside the WTC area to reinstate computer processing and related services. These are corrective controls because they replace data and services that were lost.
- 6175 reads






