A mere decade or so ago, e-business basically meant EDI. The Internet has radically changed the nature of e-business so that it has become the dominant platform for not only e-business, but EDI as well. Does this mean EDI is dying? Well, not exactly. Many experts believe EDI is here to stay and currently EDI volume continues to grow at a rate of about 15% per year. Still, the Internet shows far more potential growth—primarily from the potential seen in the emerging replacement language for EDI on the web, XML (eXtensible Markup Language). 1 XML is described in Technology Insight 4.2.
Technology Insight 4.1
From Private EDI Networks to the Internet: Management,Operational, and Control Considerations in Computer-to-ComputerBusiness Linkages
We use EDI in our examples but the benefits, costs, and control risks described below may apply to EDI using a VAN, when the Internet is the vehicle for EDI communication, or when XML is the standard at the heart of B2B transactions.
Benefits may include the following:
- Survival. Many organizations have been “forced” to implement EDI if they wished to continue doing business with certain customers. For instance, in the early days of EDI, Wal-Mart Stores and Kmart Corporation told all of their suppliers to establish EDI capability by a specified deadline if they wished to continue doing business with these retail giants.
- Improved responsiveness to customers’ needs. In some cases, EDI has lead to what are known as “quick response” replenishment systems, also known as vendor-managed inventory. In such systems, a large customer—Sears Roebuck, for instance—gives its suppliers access (through EDI communication links) to real-time, point of sale (POS) information. With that information available, the suppliers can forecast customer demand more accurately, fine-tune their production schedules accordingly, and meet that demand in a highly responsive manner.
- Elimination of data re-entry at the receiving organization reduces processing costs and accuracy is improved. To better appreciate the potential impact of this benefit, consider the fact that, according to one estimate, 70 percent of the data processed by a typical company’s computer system had been output by another computer system.
- Mailroom and other document preparation and handling costs are eliminated. For example, in the automobile industry, it is estimated that $200 of the cost of each car is incurred because of the amount of paper shuffling that has to be done.
Costs may include:
- Buying or leasing hardware and software.
- Establishing relationships with VANs or other electronic marketplaces and negotiating contracts.
- Training employees.
- Reengineering affected applications.
- Implementing security, audit, and control procedures.
Control considerations:
- Because signatures will no longer evidence authorizations, controls must ensure proper authorization. And, at some point during the process, we must authenticate that the message is sent to—and received from—the party intended and is authorized by someone having the proper authority.
- Without external, visual review, some business event data can be significantly in error. For example, a payment could be off by one decimal point! Therefore, controls must prevent rather than detect such errors.
- Given that the computer will initiate and authenticate messages, controls over the computer programs and data—program change controls and physical security (see Chapter 8)—become even more important than with traditional systems.
- Security procedures and other controls must prevent compromise of sensitive data and controls must ensure correct translation and routing of all messages.
Therefore, there must be controls to ensure that all messages are accurate, authorized, and complete.
To attain these control goals, organizations have implemented the following control plans, among others:
- Artificial Intelligence applications (see Chapter 5) may be used to determine that incoming messages are reasonable—consistent with normal message patterns—to authenticate the source and authorization for the message.
- Access to EDI applications may require a biometric security system, a smartcard, or a physical key as well as a password (see Chapter 8).
- Data encryption (see Chapter 9) may be employed to protect data during transmission.
- Digital signatures (see Chapter 9) may be used. Much like a password or other access code, the digital signature uniquely identifies who approved a business event and also helps to ensure that the EDI message was not altered during transmission.
|
Review Question Compare EDI and XML technologies. |
Today, e-business enables the computer-to-computer exchange of business event data in structured (e.g., EDI or XML) or partially structured formats, usually via the Internet, that allows the initiation and consummation of business events. In many cases, the goods or services that are contracted for through the Internet are immediately (or soon thereafter) forwarded back to the consumer via the Internet as well (i.e., when the goods or services can be provided in electronic format, such as the case with software). The Internet radically simplifies business processes by allowing the organization that is receiving and processing business event data to project template formats to business partners for easy data entry and data transmission. For instance, if you connect across the Internet with Lands’ End (a direct merchandiser of clothing—particularly warm stuff!) you see an “intelligent order form.” You are provided an entry box to type in the product number for the item you want to order. The Web page automatically takes the number and identifies what additional information is needed (e.g., for most clothing, it will be size, color, and quantity). The additional information appears in menu form for you to select from the options available (e.g., for color, the menu might show red, navy, black, white, and green). As you enter responses on your computer, the data are automatically captured and recorded on the Lands’ End computer. Technology Insight 4.3 provides some management, operational, and control issues associated with the use of the Internet for e-business, while Technology Application 4.3 provides some examples of ventures into Internet commerce.
|
Review Question How does the Interest simplify the world of e-business? |
Technology Insight 4.2
XML
Extensible Markup Language (XML) is a Web-based data format that enables information to be shared over the Web. XML provides a framework within which data from any type of source can be communicated and understood by any business partner’s system, independent of technology platform.
XML supports a tree structure in which labeled data items are hierarchically related. A simple example is an XML item in which a phrase labeled as a greeting might hail the world with the
following XML code:
Most XML standards are being established to permit common transaction processing among likeminded industries or corporate functions (e.g., buying or selling computer hardware components, or
exchanging human resources data). XML-enabled transaction processing will simplify Web transaction exchanges, and may completely replace EDI as the standard of choice as soon as reliability
and security problems have been adequately addressed. XML parsers (programs that can read XML) have been integrated into many Web browsers, Web-enabled enterprise systems (e.g., Oracle
Applications and Great Plains), and other business applications.
In a recent Zona Research Market Report, almost half of surveyed companies reported that they plan to convert some or all of their EDI applications to XML within the near future. Of the rest, half don’t use EDI presently, and the other half will stay with EDI or convert EDI dynamically to XML. XML’s usage is expected to rise from 0.5% of e-commerce transactions in early 2000 to 40% by the end of 2003. The key reasons these companies see for using XML are that XML
- Makes it easier to search for business partners or products
- Lets the company use event data for other purposes once it’s in XML form
- Shortens application development time
- Enables business processes to take less time from start to finish
- Makes it easier to convert business data to a more usable form
- Ties together multiple internal applications within the company
- Allows links with customers’ systems
- Supports links with suppliers’ and trading partners’ systems
- Allows the company to join an electronic marketplace that uses XML
Although many vendors are working diligently to release XML-based products, there remain many issues and questions to be answered before the language reaches its potential. These include security, agreement on standard formats, and senior management’s lack of understanding about its challenges and potential. XML encryption standards are in development and a draft was released in 2001.
Sources: Martin Marshall, “XML—Like the Air that We Breathe,” Informationweek, March 5, 2001, pp. 47–53; http://www.w3.org/TR/REC-xml, April 2001.
Technology Insight 4.3
E-Business Management and Operations Considerations
Benefits of Internet commerce include the following:
- Survival. Many organizations have been “forced” to implement e-business to compete in the changing nature of their industries. If they wish to remain competitive with other companies taking advantage of the Internet for commerce, they will need to venture to the Web.
- Improved responsiveness to customers’ needs. Customers expect immediate feedback and easy availability of information and help. The Internet is a useful tool for servicing customer and client needs—forming the communications medium for distributing information and support services.
- Global penetration. The Internet is generally the easiest and least expensive way to reach customers worldwide that an organization may never have been able to reach previously.
- Reduced processing costs and improved accuracy result when data are not reentered at the receiving organization. Customers now provide most of the data entry themselves, removing the need for the selling organization to key in most of the business event data.
- Mailroom and other document preparation and handling costs are eliminated. The business event data processing side of a business can operate with virtually no human intervention until it is time to prepare and deliver goods.
- The opportunity to rethink and redesign existing business processes and controls in the course of implementing e-business.
Costs of using the Internet include:
- Organizational change to a completely different way of doing business.
- Buying equipment and maintaining connection to the Internet (or leasing through a network provider).
- Establishing connections with a new set of customers.
- Staffing and training employees to work in a technology-driven environment.
- Reengineering application systems to process data acquired through the Internet.
- Maintaining security of the Internet site.
Risks of Internet commerce include:
- Hackers attempting to access sensitive information such as customer lists or customer credit card information.
- Denial of service attacks. Denial of service attacks are expected to escalate over the next few years as individuals or organizations attempt to knock out Web sites by overloading them with site visits and preventing customers or other users from gaining access. These attacks may occur simply for the challenge or frequently due to a political or other difference with the organization that hosts the site. See Technology Insight 8.3, for a fuller description.
- Trust. Increasingly, the success of B2B relationships necessitates the identification of business partners who are allowed access to sensitive internal information. A breakdown of that trust can have grave consequences to the organization making its information available.
Technology Application 4.3
General Uses of E-Business
Case 1
Office Depot is a major player in the business to consumer (B2C) space. Its Web-based sales reached $350 million in 1999, and were estimated at $800 million for 2000, or approximately 9 percent of its revenue. It is a leader in the move from “bricks and mortar” (a traditional company structure) to “bricks-and-clicks,” an organization that views the Internet as an alternative marketing channel to traditional interactions with customers. The company has garnered significant e-commerce sales agreements with many large companies such as General Electric and Procter & Gamble. In addition to permitting online sales, Office Depot also helps customers by supplying online business tools, forms, human resource handbooks, and other useful Internet links. Much of the success of the site is attributable to the integration between its distribution channels and its Order-to-Cash process (e.g., order processing and billing) in its enterprise system. The system has also formed the basis of an extranet with vendors that feeds into the Purchase-to-Pay business process. Vendors are able to set up product information in Office Depot’s enterprise system and check inventory levels at each location without human intervention, speeding replenishment and reducing stockouts.
Case 2
One type of business that is particularly compatible with e-business is one in which the goods or services can be delivered across the Internet instantaneously, much the same as payment is provided by the customer. TheStreet.com is one company that has implemented such a business plan. TheStreet.com is in the business of providing financial information that is valuable, unique, and timely. The company philosophy is that if it fails in any of these three attributes for the information it delivers, customers will stop coming. Despite the many business publications on the market, TheStreet.com has quickly risen as a leading provider of financial information by being both cheaper and timelier. It is one of the few information providers able to provide subscription service solely through the Internet. This is one form of the so-called Internet cottage industry whereby new small businesses spring up on the net to provide unique services.
Case3
Wal-Mart is one of many retailers who are setting up electronic storefronts on the Internet to sell its goods directly to customers. Wal-Mart takes the customer’s order and credit card number over the Internet, electronically processes the order, and sends the order directly to the manufacturer, who ships the product to the customer. The company’s Web site becomes little more than a for-fee electronic interface between the customer and the manufacturer.
Sources: Eric Berkman, “Clicklayer,” CIO Magazine, Volume 14, issue 8, (February 1, 2001): 92–100; Eric Hall, “Information Wants To Be Free? Not at TheStreet.com,” Infoworld(December 8, 1997): 94–96; Linda Rosencrance, “TheStreet.com Looks for Road to Profitability,” Computerworld Online (November 16, 2000); Todd R. Weiss, “Walmart.com Site Back Online After 28-day Overhaul,” Computerworld Online (October 31, 2000).
There are two primary categories of e-business over the Web: (1) business-to-consumer, or B2C (e.g., Lands’ End), and (2) business-to-business, or B2B. Figure 4.7 depicts a typical type of secure B2B arrangement. Note that the numbers in the circles are cross-references to corresponding locations in the narrative description.
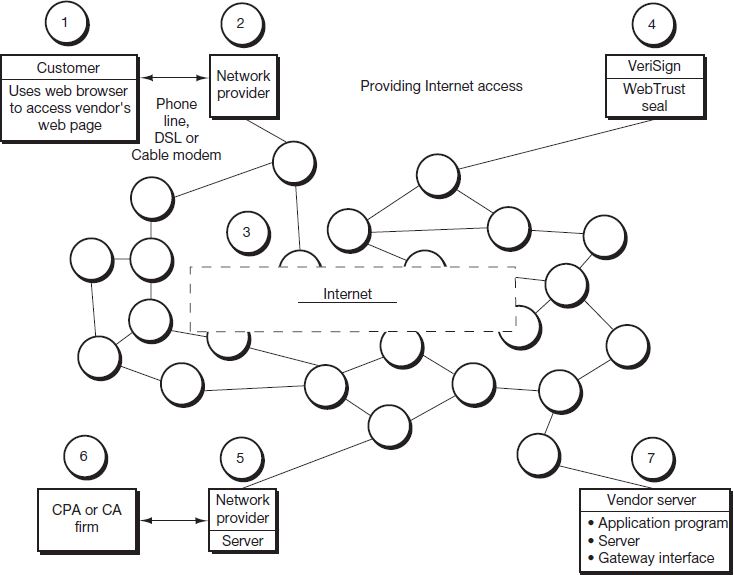
Client-Server Relationship (circles 1 and 7)

|
The connection created between the customer and the vendor is a Web-enabled extended form of client-server applications. The customer (circle 1) is the client node—dictating that during connection, the customer computer environment should be secure and essentially inaccessible via the network. The vendor (circle 7) is the server node and therefore must have the capability to receive the customer’s transmission and translate that transmission into processable data for use in the vendor’s application programs. This translation is made through common gateway interface (CGI) software. The vendor, acting as the server part of the relationship, then provides the necessary correspondence back to the customer (client) in an understandable format (i.e., an Internet-based language such as Java or XML). To use the Lands’ End example again, when you place your order, your computer should be inaccessible (i.e., secure) over the Internet, and the type of computer and software you are using will be unknown on the system. The Lands’ End computer receives your order and uses CGI to translate your message into a form their program can understand and process. Similar to EDI environments, once the business event data have been collected by the vendor, applications can be completed through any of the modes of business event data processing. For instance, Lands’ End used a periodic mode approach to process batches of sales several times an hour. 2 |
Network Providers (circles 2 and 5)
As with EDI, to participate in the business event, both parties must have the capability to communicate over the Internet. For many companies and organizations (as well as some individuals), this access comes through a direct connection between the entity’s computer networks (or a single server) and the Internet. For other companies and organizations, as well as the vast majority of individuals, it will be more desirable to gain access through a network provider.
Network providers are companies that provide a link into the Internet by making their directly connected networks available to fee-paying customers. Most network providers bring a host of other benefits along with Internet access. Common benefits include e-mail access, electronic mail boxes, space allocation for personal Web pages, and remote connection to other computer sites (e.g., telnet and FTP connection). Many organizations will also use network providers to run their servers when assuming that role in the client-server relationship. In Figure 4.7, circle 5 denotes a network provider who would be providing server management services for the CPA or CA firm denoted by circle 6. Hence, when the business event is being completed between the customer and the vendor, information from the accounting firm would be acquired from a server operated by the firm’s network provider.
|
Review Question What role do network providers play in the e-commerce environment? |
Assurance Providers (circles 4 and 6)
A major concern for most organizations and individuals participating in e-commerce has been Internet security. Security is the most critical factor that has hampered the growth of e-commerce. One early survey showed that 90% of Internet users felt increased security was necessary before they would transmit personal information (e.g., credit card information) across the Internet. 3 Many stories have circulated about the risk of credit or debit card information being pirated off the network, with large sums of money being expended by unauthorized users. Additionally, the Internet has spawned a whole array of cottage industries that have no physical storefronts, but rather are operated completely from Internet server-supported Web pages. Many Internet users are rightfully concerned about the possibility that a company may be fictitious, with the electronic storefront merely being a means by which to gather credit card and debit card information for illicit use.
|
Review Question What types of assurances are provided by Internet assurance services? |
These concerns over security have spurred the development of a new line of business—Internet assurance services. Internet assurance is a service provided for a fee to vendors in order to provide limited assurance to users of the vendor’s Web site that a site is in fact reliable and data security is reasonable. Technology Application 4.4 provides a more detailed discussion of Internet certification programs and assurance services.
Figure 4.7 demonstrates how one common type of assurance provider operates using the WebTrust program as discussed in Technology Application 4.4. The vendor (circle 7) displays the WebTrust certification seal and a reference to the assurance provider on its server Web page. When the customer accesses the vendor’s Web page, he or she can click on the WebTrust symbol to assure it continues to be applicable. Clicking on the WebTrust symbol executes a link to the VeriSign server (circle 4) for verification of the authorized use of the symbol. VeriSign verifies the symbol’s appropriate use by sending a message to the customer (circle 1). The customer can also get a report on the level of assurance provided with the certification by clicking on the Web link (contained on the vendor’s web page) for the accounting firm. Clicking this link connects to the accounting firm’s (circle 6) server—provided by its network provider in this case (circle 5)—and the auditor’s Internet assurance report for the vendor displays on the customer’s computer (circle 1).
Technology Application 4.4
Internet Security Certification
Case 1: Webtrust Certification
Like many vendors of high technology products, Westek Presentation Systems made a decision to pursue opportunities for e-commerce by taking its product lines to the Web. However, a major problem was many customers’ reluctance to purchase products over the Internet because of security issues. These security issues included concerns over whether the company really existed (or was simply a front to collect credit card numbers for fraudulent use) and over the safety of transmitting credit card information over the Internet. Westek’s CPA proposed a solution recommending that Westek have the CPA provide assurance services that would attest to the validation of the company and the safety of its Web site for potential customers. In late 1997, Westek became the first certification client for this new type of security service.
The WebTrust Seal of Assurance is the product of a joint venture between the American Institute of Certified Public Accountants (AICPA) and the Canadian Institute of Chartered Accountants (CICA). It is designed to provide comfort and assurance that a Web site is reasonably safe for users participating in B2C e-commerce. Once a site receives WebTrust certification, it should be reviewed at least every 90 days by the CPA/CA to assure adequate standards have remained in place and the site remains reasonably secure. Basically, the Web site must meet three standards:
- Business practices disclosure: The client company must disclose its business practices for conducting e-commerce to users accessing its Web page.
- Transaction integrity: The client company must have proper control procedures in place to assure that customers’ business events data are completed and billed correctly.
- Information protection: The client company must have proper controls in place to ensure customer information is protected from unauthorized use.
Recently, WebTrust certification was made available in separate components rather than requiring certification on all three of the above areas. For instance, one of the available seals now covers only business practices and transaction integrity.
Case 2: ICSA Certification
An alternative to WebTrust is provided by the International Computer Security Association (ICSA) Labs—a subsidiary of TruSecure. ICSA Labs provides reduced risk to both the customer and the vendor by providing, verifying, and improving the use of appropriate security standards across a range of critical dimensions. The Anti-Virus certification helps product developers address threats from malicious programs. The Firewalls certification is based on testing of commercially available firewall packages. Crytography certification helps users identify products that effectively use cryptography to provide security services. Intrusion Detection tests the functionality and compliance of intrusion detection products. Additionally, a new product related to Public Key Infrastructure (PKI) product certification is due out around the beginning of 2003.
Case 3: TRUSTe
Another product, TRUSTe, focuses solely on privacy issues. The TRUSTe certificate is awarded only to sites that adhere to established privacy principles of disclosure, choice, access, and security. Webstites carrying the seal also agree to TRUSTe’s prescribed dispute resolution processes for customers. The focus on privacy creates a nice market niche for TRUSTe as privacy concerns have been in the forefront of Internet legislation for many countries. TRUSTe has recently added services for compliance with the guidelines of the Children’s Online Privacy Protection Act (COPPA). The Children’s Privacy Seal Program assures Web sites are safe harbors for children to visit.
Case 4: BBB Online
The most popular certification program is the Better Business Bureau’s BBB OnLine program with 10,482 active Web sites. The program confirms a company is a member of the Better Business Bureau and that there has been a review for truth in advertisement guidelines and good customer service practices. The program is likely so popular because of the broad recognition of the Better Business Bureau and the low cost of attaining certification.
Sources: Richard J. Koreto, “In CPAs We Trust,” Journal of Accountancy (December 1997): 62–64; AICPA/CICA, “CPA/CA WebTrustsm Version 2.0” http://www.cica.ca (August 2000); ICSA, “ICSA Certified Secure Web Certification Program,” http://www.icsalabs.com (January 2002).
Internet Connection (circle 3)
To obtain an Internet connection you must have a link to one of the networks that connect to the Internet and indicate the Internet site with which the client wants to connect. A connection is then made between the client and the desired site—the server.
A couple of other issues related to the organization of the Internet and its impact on e-commerce should be noted. First, the nature of the Internet as a public network-based infrastructure has greatly leveled the field in e-business. Only fairly large businesses could afford EDI’s communications hardware and software. The creation of a public network and the subsequent creation of XML and relatively inexpensive (or even free) software for using the network have brought the costs of e-business within the ranges of economic feasibility for most small- and medium-sized entities. This change in cost structure and ease of use are the two forces driving the strong growth in e-commerce.
|
Review Question Why is EDI moving to the Internet? |
Other Internet Uses for E-Business
While we have focused in this chapter on the most common forms of e-commerce and the direct linkages between customer and vendor, a number of intermediaries are evolving that promise to bring costs down even further for organizations. Two forms that seem most likely to have long-term success are auction markets and market exchanges. These are explained in greater detail in Technology Insights 4.4 and 4.5.

|
The Internet is not only a place for completing sales, but is also an environment for improving customer support for non-Internet-based commerce. A Web page may simply be one more channel in which to advertise and market an organization’s goods and services. At the next level, it may be an arena for providing ongoing customer support. For instance, Symantec is one of many companies that provides free software upgrades over the Internet—in this case, providing monthly updates for its Anti-Virus software. In another example, many courier companies (such as Federal Express) use the Internet to allow customers to access information to track their packages at any given point and to know when they have reached their destination. Such examples of customer support have become a huge new market for major software vendors. These systems fall under the broader category of customer relationship management (CRM) systems. CRM systems provide customer self-service capabilities (i.e., let the customer inspect an account or get product help through a Web interface rather than through interaction with a support person), electronic catalogues, shipment update information, and aid the salesperson by storing an analyzable history of the customer and the customer’s past business interactions. One of the bigger challenges has been to get the CRM systems to interact with enterprise systems to share data. In an effort to improve integration, all of the major software firms are involved in initiatives to further empower CRM extensions to their enterprise systems. |
Technology Insight 4.4
Internet Auction Markets
Internet auction markets provide an Internet base for companies to either place products up for bid or for buyers to put proposed purchases up for bid. In the first case, a market participant puts an item up for bid, sets a minimum bid price, and awaits completion of the bidding process, as happens on eBay. While this market works fairly well for B2C e-commerce, it is not as effective for business-to-business commerce. For B2B e-commerce, a company may put specifications for a product out on the marketplace as a request for proposals (RFPs). Participating organizations in the market can then bid on the sales by providing a proposal that includes details on product specifications, costs, availability (i.e., timing of delivery), and logistics. The buying organization can then select the proposal that seems most desirable for meeting the organization’s needs at a minimal cost and risk.
Technology Insight 4.5
Internet Market Exchanges
Internet market exchanges bring together a variety of suppliers in a given industry and one or more buyers in the same industry. Suppliers can put their products online, generally feeding into electronic catalogs that allow the buyer(s) to sort through alternatives from different suppliers and electronically place an order. Even if only one supplier carries a certain item, efficiencies are still gained by avoiding the purchase order process (described in detail in Chapter 12) and executing an order through selection from a Web catalog. In some cases, the buyer will make its needs known on the marketplace and suppliers will review the needs and determine whether to fill the orders. The key is to make sure the market is efficient enough to assure that the buyer will get the product purchased on a timely basis for when it is needed, for example getting purchased goods to an assembly line within an hour of when needed for production. This part can get tricky and the exchange must be set up carefully.
Internet market exchanges can be either private or public. Private exchanges limit the buyers and suppliers who can participate in the market. Public exchanges bring together suppliers and buyers and allow essentially any organization to participate, subject sometimes to credit approval and background checks. Private exchanges that have been planned or are currently operating outnumber such public exchanges 30,000 to 600. However, private exchanges have drawn the watchful eye of the Federal Trade Commission (FTC), which oversees fair trade practices and potential anti-competitive practices that may result from restricting participation in the market exchange.
Source: Steve Ulfelder, “Members Only Exchanges,” Computerworld Online (October 23, 2000).
- 6722 reads







